750 words, 3 minutes.
The reason I don’t post on Cyber Security current affairs?
It’s a scramble to be first.
If I’m to write something, what should it be? What’s my angle? Which lens do I use on the microscope, or since this is a mass medium, the projector? What film can I show you that you haven’t already seen a dozen times? I’ll attempt to answer these questions here, and in so doing introduce what may become a new thread of posts.
Once you’ve read one article about a breach, vulnerability, or scandal, the marginal value of reading a second or third diminishes rapidly. The best commentators are well known and for the most part, are accurate and fair. When they make a mistake or the story changes they publish a correction. It’s a beat that rewards quick reflexes, deep Rolodexes, and the ability to form coherent bulletins from evolving, incomplete facts. I don’t have much to add to the story, even if I could get there quickly enough and hold that pace.
If you ignored 90% of the rest of the coverage little of value would be missed. The formula for most of it is simple. Just re-hashed facts and speculation. Cut and paste a pithy quote alluding to a sinister threat. End with a clumsy plug for your 6th generation Cyber Threat Forcefield™…which would have prevented this… naturally.
My recommendation for non-technical people is to read or follow Krebs and if you’re still hungry for more check Ars Technica.
Likewise, there’s plenty of good technical analysis out there. That work takes longer and tends to come from the handful of larger Cyber Security firms. Their analysts can take an uninterrupted few days away from clients to produce accurate, presentable write-ups. Reverse engineering was never really my forte. I spent more time profiling software for performance than forensics/security. While the inner workings of malware is interesting to some, most people find it too esoteric.
Kaspersky Lab (@kaspersky) and Cisco Talos (@TalosSecurity) do a better job of technical analysis than I would. Independent researchers like Rob Graham and Pepper Potts produce good work too.
If I’m to add anything useful, I’ll need to set some criteria for quality control.
Quality Control
These are the intrinsic, authentic characteristics of all my posts. Any of my future posts on Cyber Security current affairs must:
- Have relevance after the present moment in time.
- Have value outside of the current event or incident.
- Be accretive to, or better compounds with, my future posts.
- Add value to the best of what’s already available.
- Carry little risk of inaccuracy, or factual error.
- Focus on the underlying systems driving the observable phenomena.
These criteria are the other part of the reason I haven’t posted on Cyber Security current affairs before. Difficulty.
The Lens & Themes
As for which lens to use, the answer is to be found in another recent post. Structural Realism is the lens I’ve found most useful in predicting the future. As for how Cyber Security fits with Geopolitics and the other themes of this blog, this sketch provides context. It’s called an “ikigai” (生き甲斐):
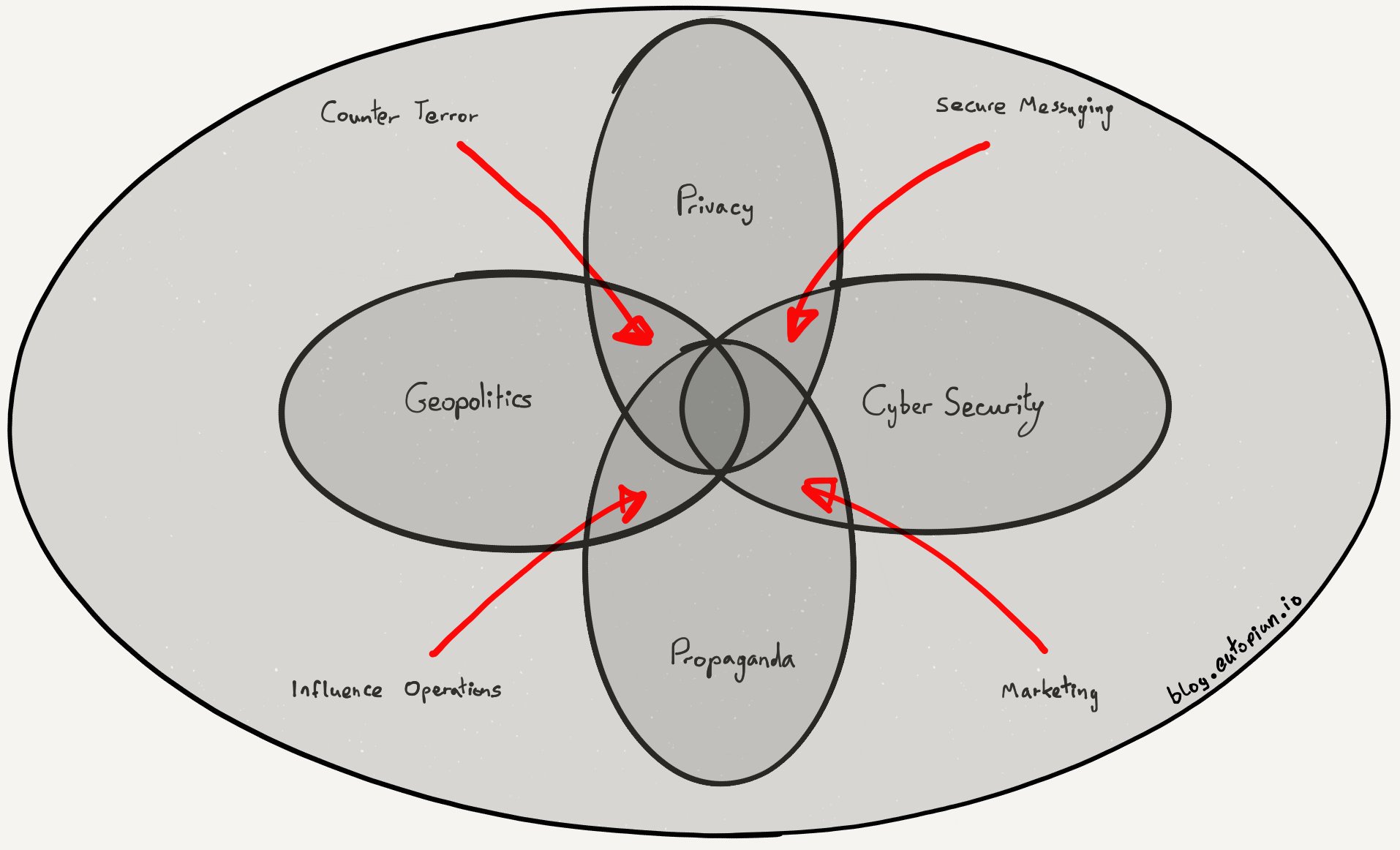
The Story
Each event has its own story. However, my posts will all ultimately be about power. They will be about the great forces and constraints shaping our world. The popular commentators will describe an individual leak, breach, or scandal, but these are just surface ripples. I’ll reveal the deep ocean currents producing these events. I’ll describe why they are occurring and who they benefit.
Most people don’t follow Cyber Security in anything other than a casual way. For them, isolated incidents come and go like waves of a fever. I’ll explain the connections between them and the second order effects and omissions.
It will be a tale of H-Diagrams1, Strategic Software2, Geopolitics3, and Propaganda. Speaking of which, I’ll avoid the exaggeration and distortion used by vendors, politicians, and journalists.
The Cast
The cast includes state and non-state actors. It features corporations with revenues and market caps larger than some countries. Some may be masked but we can discern their character from their actions and the results those actions ultimately produce.
Breaking The Fever
I’ll help you see more clearly by understanding the context in which these events take place. The heroes and villains might not be clear as they are in Hollywood, but in the end, you’ll have a Grand Narrative within which to place them. Not just a series of walk-on parts in isolated episodes.
First up will be the March/April 2019 leak of information and tools from APT34, also known as Oilrig or HelixKitten, then the Huawei 5G debacle. So take a seat, the film is starting. We’re going to Iran.